Event Logging - The Rise of Burst Signals
The Increasing Importance of Event Logging in TSCM Bug Sweeps
In the digital age, where technology has become an integral part of our lives, ensuring the security and confidentiality of sensitive information has become more critical than ever before.
Technical Surveillance Countermeasures (TSCM) bug sweeps, are essential for detecting and neutralizing covert eavesdropping devices that pose a significant threat to privacy and security.
Among the various techniques employed in TSCM;
Event logging, has emerged as a vital component to enhance the effectiveness and thoroughness of bug sweeps.
This editorial will explore why performing event logging in TSCM is now more critical than ever.
Evolving Threat Landscape:
The threat landscape has evolved rapidly in recent years, with sophisticated eavesdropping devices and surveillance techniques becoming increasingly accessible.
IOT enabled systems with WIFI and or GSM connectivity, combined with audio and video capture, are widely available.
Traditional Live TSCM sweeps focused primarily on physical inspections but many protection surveys fail to address the potential risks posed by advanced digital surveillance methods.
Common Reasons why Event logging May not be Performed:
Deploying Event Logging systems on site means more time on site, this increases the cost of a full sweep that factors event logging as a threat.
- Expensive Event logging Systems
Traditionally, Event Logging systems were expensive kit, most TSCM specialists do not want to leave a system on site unmanned for security concerns in relation to the device.
On the other hand their clients are also reluctant to provide assurances and cover in the event a device is damaged lost or stolen, whilst onsite.
Most event logging systems are in the price range of $7000 upto $25000.
TSCM specialists can struggle to get systems on site for many of the reasons mentioned above but also because it is not feasible for many specialists to have so many high cost systems available.
Clients and even TSCM operatives may not be fully aware of the change in the threat landscape, Event logging is traditionally associated with Threat Level 7+ types of sweeps.
The rapid advancement of IOT enabled devices has pushed what was once considered a sophisticated threat, into a standard one, that is easily accessible and poses a threat to organizations of all sizes.
BH04PRO was designed to overcome many of the issues outlined above.
- PBN-BH04 PRO is a sub $2000 system.
- The Small compact system can be easily deployed on site unmanned.
- The low cost of this system overcomes the risks associated with leaving kit on site and a clients concerns over the devices security whilst on site
- This system being left onsite unmanned lowers the cost of the inspection and alleviates the need for a TSCM specialist to be on site while event logs are being recorded.
- Specialists can deploy multiple systems in multiple client locations due to competitive cost and reduced risks, associated with this system, compared to higher cost systems
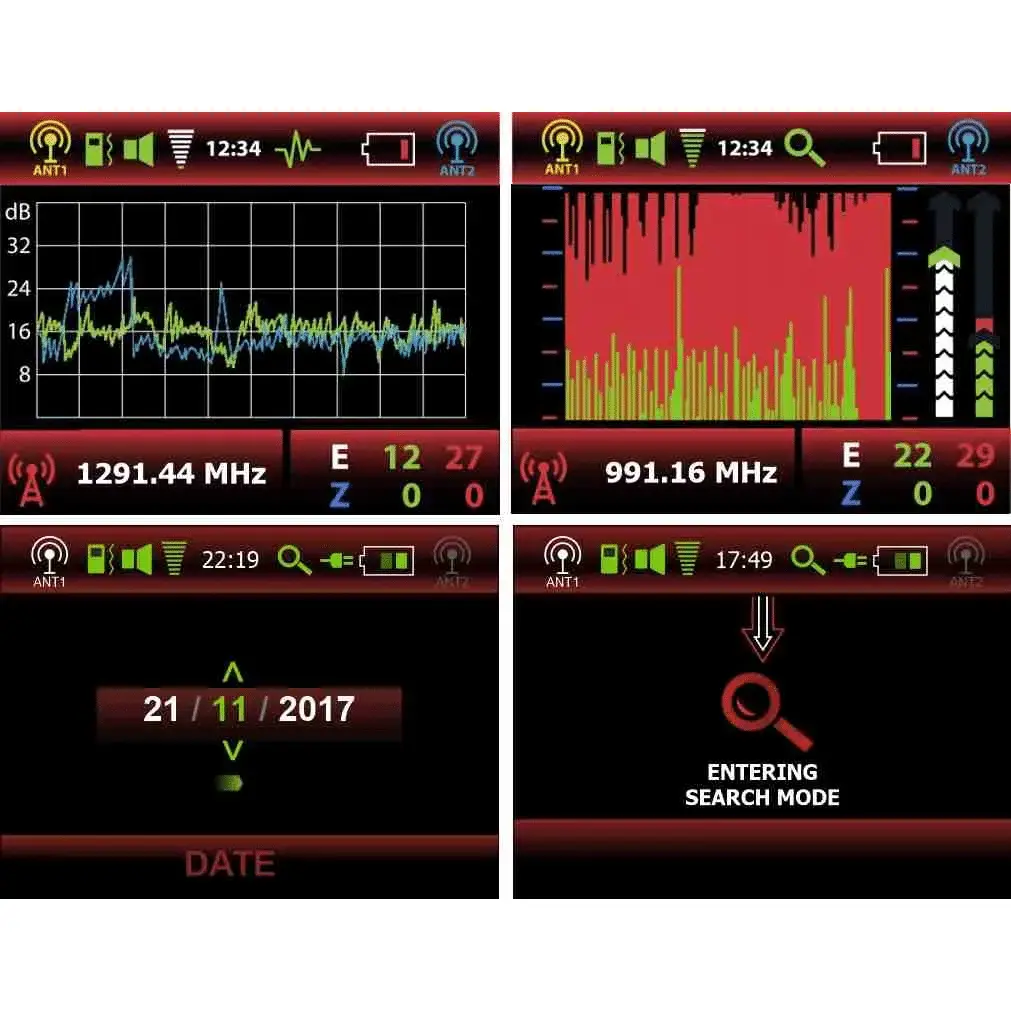
The Advanced Digital Threats in Sleep Mode 95% of the Time
What is an Advanced Digital Surveillance tool?
One such bugging device which utilizes a burst transmission is a Store & Forward Audio/Video recorder.
This type of system collects recordings at specific times and stores them until they are activated or remotely configured to transmit the collected data.
Used correctly, this type of eaves dropping system will be configured to transmit data at an irregular time, out of office hours, when the WIFI or GSM transmission is least likely to be detected.
Systems like this, especially audio, need only a few minutes to transmit data and these systems can normally hold hundreds of hours of file storage with long life batteries, meaning they can be concealed for months on end on a single charge.
Advanced digital surveillance tools are no longer difficult to procure, these systems can be purchased online in any country in the world.
There is no specialist company producing the majority of these threats, there are thousands of options.
By incorporating Event logging in every sweep, TSCM specialists can fully factor the potential threat of Burst signal systems as described above.
How do Threats penetrate an Organization?
Insider Threats:
Insider Threats are one of the most common reasons a security breach occurs within an organization.
The ease of access and opportunity to deploy eaves dropping devices into a companies confidential quarters is easier for someone like a disgruntled employee or even an employee working hand in hand with a companies rival.
Disgruntled employees are just one example, here is a range of threats that can occur from the inside:
Competitors:
Business rivals seeking to gain a competitive advantage might attempt to gather sensitive information about the company’s products, strategies, or upcoming projects.
Disgruntled Employees:
Current or former employees who hold grudges against the company may try to sabotage its operations or steal confidential data.
Industrial Spies:
Organizations or individuals, sometimes from foreign entities, looking to gain strategic or technological intelligence by infiltrating the company’s premises.
Cybercriminals:
Criminal groups or hackers seeking to exploit vulnerabilities in the organization’s security for financial gain or to access valuable data.
What can we learn from Event logging Systems like BH04PRO?
Digital Footprints:
In today’s interconnected world, every action leaves a digital footprint.
Event logging in TSCM involves capturing and recording various system events, including authorized and unauthorized transmissions.
These digital footprints act as a forensic trail, allowing investigators to reconstruct activities and identify any anomalies or suspicious behaviors.
By meticulously analyzing event logs, TSCM professionals can uncover hidden patterns and uncover potential security breaches that might otherwise go undetected.
Proactive Threat Detection:
Event logging empowers TSCM specialists to adopt a proactive approach to threat detection.
Instead of relying solely on physical inspections & reactive measures, event logs provide a continuous monitoring mechanism.
Real-time analysis of event logs enables the identification of unusual or unauthorized activities, such as unexpected network connections, and abnormal data transmissions.
By detecting potential threats in their early stages, TSCM practitioners can swiftly respond, mitigate risks, and protect sensitive information.
Auditing and Compliance:
Event logging plays a crucial role in maintaining compliance with regulations and industry standards.
Organizations in sectors such as finance, healthcare, or government often have strict data protection requirements.
By implementing comprehensive event logging practices, organizations can demonstrate due diligence, comply with regulatory obligations, and meet audit requirements.
Event logging monitoring & Detection serves as a valuable source of evidence in the event of a security incident or breach, facilitating investigations and supporting legal proceedings.
With an Event Logging system in place, users may be able to identify when a breach occurred.
Note:
Event Logging for Compliance is normally introduced as a result of a data breach event that has already occurred within an organization.
Event Logging systems provide TSCM professionals with an opportunity to become part of the ongoing threat protection plan within an organization as opposed to a reactive one.
PBN-BH04 PRO Introduction in North America
Since 2021 PBN-Detect has supplied over 230 Investigation Agencies with the PBN-BH04PRO Event Logging TSCM Detector.
The solution has been demonstrated at multiple industry events including TALI, CALI & SCALI and is available at many specialist security stores around the country.
Conclusion:
As the threat landscape continues to evolve, the inclusion of event logging in TSCM bug sweeps has become paramount.
Event logging has the ability to capture digital footprints, enable proactive threat detection, ensure compliance, and support forensic analysis, event logging offers a comprehensive, highly competitive and powerful tool for TSCM practitioners.
Embracing event logging as an integral part of TSCM protocols will enhance security measures, safeguard sensitive information, and provide organizations with the peace of mind they need in an increasingly connected world.